
Getting Started With Network Traffic Monitoring Fundamentals
Network traffic monitoring is essential for maintaining a healthy and secure network infrastructure. It involves capturing, analyzing, and interpreting the flow of data across your network. This helps businesses ensure optimal performance and robust security. For example, understanding traffic patterns allows organizations to identify bottlenecks, optimize bandwidth allocation, and enhance user experience. Network traffic monitoring isn’t just a technical function—it’s a business imperative.
Core Components of Network Traffic Monitoring
Several key components form a comprehensive network traffic monitoring system.
- Data Collection: Gathering data through methods like packet sniffing and flow analysis. This provides raw information about network activity.
- Analysis: Processing and interpreting collected data to identify trends, anomalies, and potential issues. Tools may utilize techniques like deep packet inspection for a detailed view.
- Alerting: Notifying administrators about critical events or when performance thresholds are exceeded, enabling proactive intervention.
- Reporting: Generating reports and visualizations to offer insights into long-term network health and performance. This allows for informed decisions on network optimization and capacity planning.
Why Traditional Approaches Fall Short
Traditional reactive approaches to network management are no longer sufficient. Simply waiting for users to report issues results in lost productivity and decreased customer satisfaction. Traditional methods often lack the detail needed to identify subtle performance issues or security threats.
Benefits of Proactive Network Traffic Monitoring
Proactive network traffic monitoring empowers IT teams to address issues before they affect users. This results in:
- Improved Network Performance: Identifying bottlenecks and optimizing bandwidth usage.
- Enhanced Security: Detecting and mitigating security threats immediately.
- Reduced Downtime: Proactive problem resolution minimizes service disruptions.
- Better Capacity Planning: Using data-driven insights to plan for future network growth.
By investing in comprehensive network traffic monitoring, businesses can build a robust, secure, and high-performing network infrastructure. This proactive approach is crucial for supporting continued development and ensuring business success in a competitive market.
Why Network Monitoring Has Become Business-Critical

The demands placed on network teams have changed drastically. This isn’t just a passing trend; it’s a complete reshaping of how businesses function and their dependence on robust networks. As a result, network traffic monitoring has become a vital business operation, moving from a useful tool to an absolute necessity. This is particularly evident in the AE region, where rapid technological progress and increasing use of digital services are pushing network infrastructure to its limits.
The Challenges of Modern Network Management
Today’s network environments face extraordinary hurdles. The explosion of data traffic, the growing reliance on mobile devices, and the widespread adoption of cloud technologies introduce complexities that traditional monitoring methods struggle to address.
For instance, the rise of remote work and the increasing number of connected devices mean networks must handle significantly more data than ever before. This underscores the importance of investing in strong monitoring solutions to maintain optimal performance. Further complicating matters, these new technologies and usage patterns create new security vulnerabilities, making advanced monitoring for threat detection essential.
In the UAE and the wider Middle East and North Africa (MENA) region, network traffic monitoring is especially crucial. The region has experienced explosive growth in mobile data usage, driven by widespread smartphone adoption and the increasing availability of high-speed internet.
By the end of 2024, average monthly mobile data traffic in the MENA region was around 10.36 exabytes, with projections showing a rise to 28.34 EB per month by 2029. This enormous surge in data traffic demands sophisticated monitoring tools to manage network resources effectively and prevent potential outages. You may also find this resource useful: How to master Cyber Security.
The Importance of Proactive Monitoring
Given these growing challenges, organizations are increasingly focusing on proactive network traffic monitoring. This approach involves continuous analysis of network activity to identify and address issues before they impact users.
Rather than simply reacting to problems, proactive monitoring anticipates and mitigates potential threats and bottlenecks. This shift demonstrates a growing awareness of the direct link between network performance and business success.
Furthermore, with the rising frequency of data breaches and cyberattacks, organizations understand that robust network traffic monitoring is no longer a best practice, but a fundamental requirement for maintaining security and business continuity. Downtime translates to substantial financial losses and damage to reputation, making proactive monitoring a vital investment. Effective network traffic monitoring is no longer optional; it’s essential.
Choosing The Right Network Traffic Monitoring Tools
Selecting the right network traffic monitoring tools can feel overwhelming. This section helps you confidently evaluate and choose the best tools for your needs, from free open-source options to robust enterprise platforms. We’ll cut through the marketing and focus on practical, real-world considerations.
Key Considerations When Selecting a Tool
Before exploring specific tools, define your monitoring needs. Are you focused on performance optimization, security threat detection, or meeting compliance requirements? Your organization’s priorities will determine the right tool.
- Scalability: Can the tool handle your current and future network size? A tool suitable for a small network might not work for a large enterprise.
- Integration: Does it integrate with your existing IT infrastructure and other monitoring tools? Seamless integration simplifies management and improves efficiency.
- Ease of Use: A user-friendly interface and intuitive reporting are crucial for efficient monitoring.
- Alerting and Reporting: Customizable alerting and comprehensive reporting enable proactive management.
- Cost: Balance features and budget. Open-source tools offer cost-effective solutions, while enterprise platforms provide advanced features at a higher cost.
Comparing Popular Network Traffic Monitoring Tools
Many network traffic monitoring tools exist, each with strengths and weaknesses. For a deeper dive, check out our article on Choosing Network Monitoring Tools. Here’s a brief comparison:
To help you choose the best tool for your needs, we’ve compiled a comparison table of popular network traffic monitoring tools:
Network Traffic Monitoring Tools Comparison: Comprehensive comparison of popular network monitoring tools including features, pricing models, and ideal use cases
| Tool Name | Key Features | Deployment Model | Best For | Pricing Range |
| Wireshark | Deep packet inspection, protocol analysis, open-source | On-premises | Troubleshooting, security analysis | Free |
| SolarWinds Network Performance Monitor | Real-time monitoring, performance analysis, customizable alerts | On-premises, cloud | Large enterprises, complex networks | $$ – $$$$ |
| PRTG Network Monitor | Bandwidth monitoring, device monitoring, flexible alerting | On-premises, cloud | Small to medium businesses | $$ – $$$ |
| Datadog Network Performance Monitoring | Cloud-native monitoring, infrastructure monitoring, application performance monitoring | Cloud | Cloud-based environments, DevOps | $$ – $$$$ |
This table highlights key differences in features, deployment models, and pricing, allowing you to quickly identify potential solutions based on your requirements. Remember to consider your specific needs and budget when making your final decision.
Visualizing Network Traffic Data
Understanding network traffic requires effective data visualization. The infographic below shows a 24-hour network traffic volume line graph and a protocol usage distribution pie chart (HTTP, HTTPS, and DNS).
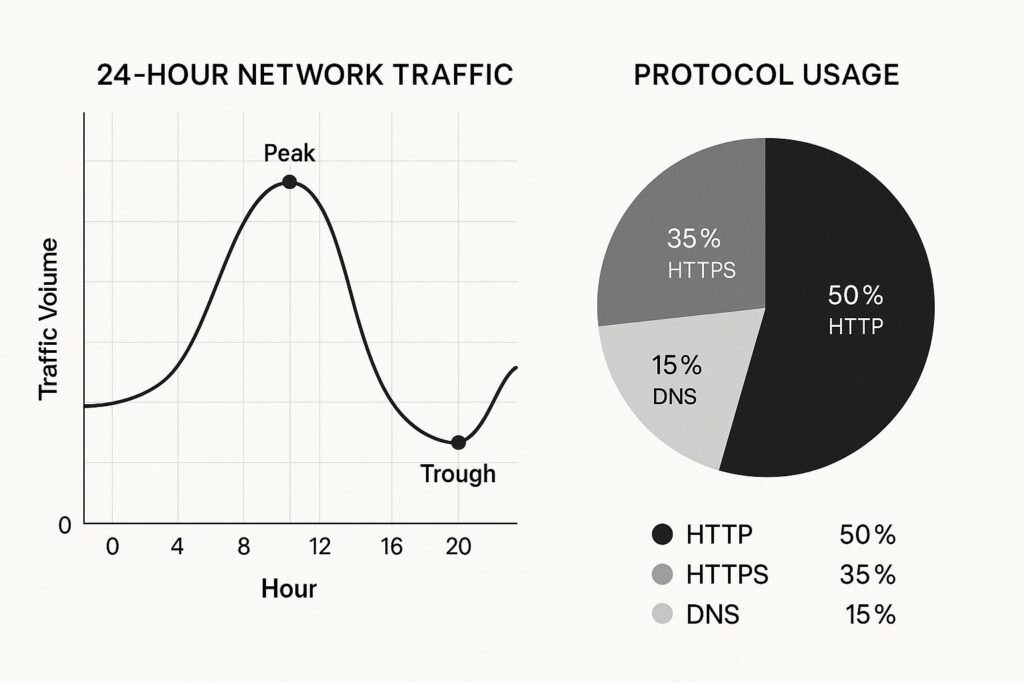
The line graph reveals peak traffic hours, highlighting high network activity periods. The pie chart shows the traffic proportion for different protocols, indicating areas for optimization or security investigations. This visualization demonstrates the importance of tools with strong reporting.
The Role of AI and Machine Learning
Many modern tools incorporate AI and machine learning. These technologies automate anomaly detection and predictive analysis, proactively identifying potential problems. However, differentiate genuine capabilities from marketing hype when evaluating tools with these features. Choose solutions with proven real-world effectiveness.
By considering these factors and researching available tools, you can choose network traffic monitoring tools that support your organization’s needs and goals, optimizing performance, improving security, and ensuring smooth operations.
Detecting Real Threats Through Smart Traffic Analysis

Modern cybersecurity depends significantly on analyzing network traffic to swiftly identify and neutralize threats. Network traffic monitoring serves as your initial line of defense, catching sophisticated attacks that frequently bypass traditional security measures. This is particularly important in the AE region, a burgeoning center for digital innovation and, therefore, a prime target for cybercriminals.
Identifying Common Cyber Threats in the AE Region
Organizations in the AE region encounter a variety of cyber threats, from ransomware and phishing attacks to Advanced Persistent Threats (APTs) and insider threats. Network traffic monitoring systems can be set up to detect unusual activity that suggests these threats.
For instance, a sudden increase in outgoing traffic to an unfamiliar location could indicate a data breach. Furthermore, unusual login attempts at odd hours or access to sensitive data by unauthorized personnel can be flagged by examining network logs. This proactive strategy enables security teams to react promptly, reducing potential damage. You might be interested in: Troubleshooting Network Issues.
Distinguishing Between Normal Traffic and Security Incidents
Using network traffic monitoring effectively requires differentiating between normal network activity and actual security incidents. This involves creating baselines of typical traffic patterns.
Any substantial divergence from these baselines, like unusual port activity or unexpected communication protocols, triggers alerts for further examination. This is comparable to knowing your typical body temperature; a rapid increase signals a possible health issue. Establishing these baselines is therefore crucial for accurate threat detection.
The Power of AI and Machine Learning in Threat Detection
Traditional security tools generally depend on signature-based detection, which recognizes known threats according to pre-set patterns. However, this method struggles with detecting new and evolving threats.
This is where AI and machine learning become essential. These technologies examine network traffic for anomalies and unusual behaviors that may indicate previously unknown threats. They learn typical traffic patterns and can detect subtle deviations potentially signaling malicious behavior, significantly improving threat detection abilities.
The UAE, in particular, has witnessed significant growth in adopting these advanced analytics solutions. Between 2019 and 2028, the UAE, as a component of the Middle East and Africa network traffic analytics market, registered a compound annual growth rate (CAGR) of 24.86% for these solutions, according to Triton Market Research. This considerable growth is fueled by the region’s susceptibility to cyber threats and the resulting demand for advanced monitoring tools.
Proactive Security Through Continuous Monitoring
Through consistently monitoring network traffic, security teams acquire valuable insights into potential threats. This allows them to proactively identify weaknesses, bolster security protocols, and react quickly to incidents.
This constant vigilance is critical in today’s ever-changing threat environment. This proactive strategy transforms network traffic monitoring from a basic observation tool into a powerful instrument for upholding robust cybersecurity.
Implementation Strategies That Actually Work
Moving from reactive troubleshooting to proactive network traffic management requires practical, effective strategies. This section outlines a step-by-step approach to implementing network traffic monitoring, from initial assessment and planning to continuous optimization. We’ll discuss how to gain real value from your tools and avoid common mistakes.
Initial Assessment and Planning
Before implementing any monitoring solution, a comprehensive assessment of your current network infrastructure is essential. This involves identifying key network devices, understanding your traffic patterns, and defining your monitoring goals. Are you primarily focused on performance, security, or both? Clearly defining these goals from the outset ensures that your chosen tools and strategies align with your organization’s specific needs.
This initial assessment provides a solid foundation for successful implementation.
Step-by-Step Deployment
Effective deployment relies on a structured approach. First, select the appropriate monitoring tools based on your initial assessment, making sure they integrate with your existing systems. Then, configure these tools to collect the necessary data, focusing on relevant metrics. Establishing baselines of normal network activity is key for effectively identifying anomalies later. Finally, thoroughly test the entire system to validate its accuracy and responsiveness.
This methodical approach prevents costly rework later on.
Ongoing Optimization and Scaling
Implementation is an ongoing process. Network traffic monitoring requires continuous optimization and scaling. Regularly review collected data, looking for patterns and areas for improvement. As your network infrastructure expands and changes, adapt your monitoring tools and strategies accordingly. This will ensure your system remains effective and provides ongoing value. For more information on maintaining a reliable network, take a look at our guide on reducing network downtime.
Managing Stakeholder Expectations
Open communication is critical to successful network traffic monitoring. Keep stakeholders informed throughout the implementation process and set realistic expectations for outcomes. Regularly share reports and insights gathered from the monitoring data, highlighting the value of your work. This helps build trust and support for continuous improvement initiatives.
Avoiding Common Pitfalls
Many organizations encounter common obstacles during implementation. Alert fatigue, triggered by excessive unnecessary alerts, can desensitize IT teams to real problems. Deploying costly tools without a defined strategy can also lead to wasted resources. Focusing on actionable insights and avoiding these pitfalls will maximize the effectiveness of your monitoring system. Careful planning and ongoing optimization are crucial for long-term success.
Building a Culture of Proactive Management
Implementing network traffic monitoring cultivates a culture of proactive management within your IT team. This proactive approach empowers your team to identify and resolve issues before they impact users, improving network performance and preventing expensive downtime. By embracing this approach, organizations can effectively handle increasing demands and maintain a competitive edge.
Optimizing Performance Through Data-Driven Insights

Effective network traffic monitoring is more than just a security measure. It’s a powerful tool for optimizing performance and strategically planning for future capacity, directly impacting your bottom line. This data-driven approach provides crucial information on network usage, bottlenecks, and growth trends affecting both user experience and business operations.
This is particularly important in regions with rapidly expanding digital economies and high user expectations.
Analyzing Traffic Flows for Optimization Opportunities
Monitoring data reveals exactly how your network resources are being used. This visibility is key to identifying bottlenecks, the points of congestion that slow down network traffic. Think of it like rush hour traffic on a highway. Identifying the choke points allows for solutions that improve traffic flow. Similarly, identifying network bottlenecks helps optimize bandwidth allocation, prioritize critical applications, and improve overall network performance.
Understanding network usage patterns also reveals areas for improvement. For example, consistently high traffic to specific servers during certain times could indicate a need for load balancing or server upgrades. This proactive approach addresses potential problems before they impact users or operations.
Predicting Future Infrastructure Needs
Network traffic monitoring isn’t just reactive; it’s predictive. By analyzing historical trends and growth patterns, you can accurately forecast future bandwidth requirements and plan infrastructure upgrades accordingly. This predictive capability enables organizations to scale their networks smoothly and efficiently, avoiding costly downtime and ensuring future growth can be handled.
This is especially relevant in areas with ongoing investment in digital infrastructure. Robust monitoring is essential to support this growth.
Data-Driven Decision-Making for Network Investments
Network upgrades and expansions require significant investment. Monitoring data provides the evidence needed to justify these expenditures, demonstrating a clear return on investment (ROI). Showing how increased bandwidth improves application performance or reduces downtime can help secure funding for these projects. This data-driven approach ensures that investments are strategic and align with business goals.
To further illustrate the importance of monitoring key network metrics, let’s look at some typical performance indicators, their normal ranges, and thresholds for warning and critical alerts. The following table provides a general overview and can be adapted to specific network environments.
Network Performance Metrics and Thresholds
| Metric | Description | Normal Range | Warning Threshold | Critical Threshold | Measurement Frequency |
| Latency | Delay in data transmission | < 150ms | 150-250ms | > 250ms | Continuous |
| Packet Loss | Percentage of data packets lost during transmission | < 1% | 1-5% | > 5% | Continuous |
| Bandwidth Utilization | Percentage of available bandwidth used | < 80% | 80-90% | > 90% | Continuous |
| CPU Utilization (Network Devices) | Percentage of CPU resources used by network devices | < 70% | 70-85% | > 85% | Every 5 minutes |
| Memory Utilization (Network Devices) | Percentage of memory resources used by network devices | < 75% | 75-90% | > 90% | Every 5 minutes |
This table highlights key metrics for maintaining optimal network performance. Regularly monitoring these indicators and setting appropriate thresholds is crucial for proactive network management.
The Middle East and Africa data center market, valued at USD 8.63 billion in 2024, is projected to reach USD 19.89 billion by 2030. Read the full research here. This underscores the increasing importance of data-driven decisions in infrastructure planning. For more insights, check out our guide on IT Infrastructure Monitoring in MEA.
This data-driven approach transforms network traffic monitoring into a strategic asset. It provides valuable insights that drive informed decisions about upgrades, bandwidth allocation, and infrastructure investments. By optimizing network performance, organizations enhance user experience, increase efficiency, and gain a competitive advantage.
Key Takeaways For Network Monitoring Success
Building a successful long-term network monitoring strategy takes more than simply selecting the right tools. It requires a comprehensive approach that includes planning, implementation, ongoing optimization, and a clear understanding of your business goals. This section offers a practical roadmap for achieving lasting success with network traffic monitoring.
Building a Foundation for Success
The foundation of any successful network traffic monitoring initiative is a well-defined plan. Begin by outlining your objectives. What are you hoping to achieve? Are you primarily focused on performance optimization, security threat detection, or regulatory compliance?
Knowing your goals will guide your next step: assessing your current network infrastructure. Understand your existing hardware and software, identify key devices, and map your traffic patterns. This knowledge will inform your choice of monitoring tools and strategies.
Choosing and Implementing the Right Tools
Choosing tools that align with your needs is critical. Consider factors like scalability, integration with current systems, ease of use, and budget. Don’t get caught up in marketing hype; prioritize functionality. Cisco offers a range of networking solutions that can be integrated into a monitoring strategy.
After choosing your tools, implement them methodically. Start with a pilot project to test configurations and refine your approach before a full-scale deployment. This allows you to identify and address any potential problems early.
Training Your Team for Effective Monitoring
Even the best tools are useless without a skilled team to operate them. Invest in training your staff on using the chosen tools, interpreting data, and responding to alerts. This empowers them to leverage your monitoring system’s full capabilities.
Ongoing professional development will keep your team’s skills current as technology advances.
Continuous Optimization and Adaptation
Network traffic monitoring isn’t a one-time setup. Networks are dynamic, and your monitoring strategies need to adapt. Regularly review your monitoring data, looking for areas to improve. Are your alerts effective? Are you capturing the right metrics? Is your system scaling with your network’s growth?
Stay informed about new technologies and best practices. Regularly evaluating and updating your tools and techniques ensures your system remains effective.
Measuring ROI and Justifying Investments
Demonstrating the value of network monitoring to leadership is essential for continued investment. Focus on metrics that align with business objectives. Show how improved network performance has increased productivity or how proactive threat detection has prevented costly security incidents. These tangible benefits highlight the positive impact of your efforts.
Staying Ahead of the Curve
The technology landscape is constantly changing. Staying informed about emerging trends, such as cloud technologies and the Internet of Things (IoT), will ensure your system stays relevant. These advancements bring new challenges and opportunities that your monitoring strategies should address.
By implementing these key takeaways, you can transform network traffic monitoring into a strategic asset, allowing your team to shift from reactive troubleshooting to proactive management. This improves performance, enhances security, and drives business value.
Ready to improve your network monitoring? Explore how FSI Technology, a leading Cisco solution provider in the UAE, can help you achieve long-term success.
