
The Power of Network Access Control: Beyond Basic Security

Network Access Control (NAC) is more than just a security feature; it’s the foundation of a strong defense strategy. It has grown from basic login controls to complex systems that adapt to an organization’s specific security needs. Security teams are using NAC to create flexible, responsive defenses that protect without impacting productivity.
This proactive approach is especially important in the Middle East and Africa (MEA) as digital infrastructure expands. The MEA network security market, which includes NAC, reached approximately USD 1,759.5 million in 2023. It’s expected to grow at a 12.5% CAGR from 2024 to 2030. This growth is driven by rising cybersecurity concerns, regulatory requirements, and the expanding digital environment in countries like the UAE.
Real-World Impact: NAC in Action
Real-world examples highlight NAC’s effectiveness in preventing major breaches. By isolating compromised devices, NAC stops malware from spreading across a network, minimizing both damage and downtime. NAC also limits access to sensitive data based on user roles, reducing the risk of insider threats and data leaks. These preventative measures are vital for maintaining business operations and protecting confidential information.
The Business Case for NAC
Beyond preventing security incidents, NAC strengthens an organization’s overall security posture. This builds trust with clients, enhances reputation, and can even offer a competitive edge. This is especially relevant in the AE region, where trust and a strong reputation are critical for business success. A robust NAC solution can also simplify compliance with regulations, reducing the risk of legal problems and penalties. For those interested in learning more, here are some of the Best Network Security Solutions in UAE.
Measuring NAC Effectiveness
Implementing NAC isn’t enough. Organizations need clear metrics to measure its effectiveness beyond simple compliance checklists. These metrics should align with both business objectives and security goals. For instance, tracking the number of blocked unauthorized access attempts can reveal valuable insights into the system’s performance.
Beyond Compliance: A Proactive Approach
NAC’s real strength lies in its ability to go beyond basic security checks. Integrating NAC with other security tools and using features like behavioral analytics transforms it into a proactive defense system. This allows organizations to identify and address threats before they can cause serious damage. This proactive approach isn’t just recommended; it’s essential for navigating today’s complex threats. This leads to fewer security incidents and a more resilient security infrastructure, allowing organizations to concentrate on growth and innovation.
Building Blocks: Critical Components of Elite NAC Systems
Effective network access control (NAC) hinges on the right combination of components working together. Understanding these building blocks is crucial for robust security. This section explores the essential elements security leaders are prioritizing for their NAC architectures.
Core Components and Their Functions
A robust NAC solution isn’t a single product but a system of interconnected components. These components work together to identify, authenticate, authorize, and manage devices and users attempting to access your network. Let’s examine these key elements:
To better understand these core components, let’s look at the following table:
Core Components of NAC Systems
| Component | Primary Function | Security Benefits | Implementation Considerations |
| Policy Enforcement Point (PEP) | Enforces NAC policies on network devices like switches and routers, controlling access based on PDP decisions. | Acts as the final gatekeeper, preventing unauthorized access. | Requires sufficient configuration and regular firmware updates to avoid vulnerabilities. |
| Policy Decision Point (PDP) | Evaluates authentication information and applies policies to determine access grants. | Centralized policy management and enforcement. | Integration with authentication servers and other security systems is critical. |
| Authentication Server | Verifies the identity of users and devices. | Ensures only authorized users and devices gain access. | Supports various authentication methods, from simple directories to multi-factor authentication (MFA). |
| Network Access Client (NAC client) | Software on endpoint devices that communicates with the NAC system, providing device information and enforcing policies. | Enhanced visibility and control over endpoint security posture. | Requires client deployment and management. |
This table summarizes the core components, their functions, and key considerations for implementation. Choosing the right components is the first step toward building a robust NAC system.
Integration for Enhanced Security
The true power of NAC lies in its integration capabilities. Combining NAC with solutions like vulnerability scanners and endpoint detection and response (EDR) provides a more comprehensive security posture. This integration allows for automated threat responses and streamlines security management. You might be interested in: How to master Cyber Security Services in Dubai.
Addressing the Weakest Link
The Policy Enforcement Point (PEP) can often become a vulnerability. Insufficient configuration or outdated firmware can create weaknesses that attackers might exploit. Prioritizing regular updates and thorough configuration is critical for maintaining effective security, ensuring consistent policy enforcement, and protecting your network.
Prioritizing Investments Based on Maturity
The ideal NAC components depend on your organization’s security maturity level. A smaller business might start with a simpler NAC solution focusing on basic authentication and access control. Larger organizations with more complex networks might require advanced features like behavioral analytics and integration with existing security information and event management (SIEM) systems. Choosing the right components ensures a secure and efficient network environment.
Implementing Network Access Control Without Disruption

Successfully deploying network access control (NAC) in the Middle East and Africa (MEA) requires careful planning and execution. Practical, proven strategies are essential for minimizing disruption to daily operations. This section offers a practical guide for security teams beginning their NAC journey.
Phased Implementation For Minimal Disruption
A phased approach is often the most effective way to implement NAC. This allows organizations to gradually introduce NAC functionalities. Starting with less critical systems and expanding coverage over time minimizes disruption. It also allows teams to address unforeseen challenges in a controlled manner.
For example, an organization might start by implementing NAC for guest Wi-Fi access. Then, they could extend it to more sensitive internal networks later. This phased approach allows for a smoother transition and builds confidence in the system.
Addressing Legacy System Compatibility
Integrating NAC with existing legacy systems can be a roadblock. A thorough compatibility assessment before implementation is vital. This assessment should identify potential conflicts and determine any necessary adjustments. Exploring NAC solutions with flexible integration options can also ease the transition and ensure a more seamless implementation. This proactive approach avoids unexpected downtime and costly rework.
Gaining Executive Buy-In And User Adoption
Securing executive buy-in is crucial for successful NAC deployment. Clearly communicating the benefits of NAC is essential. These benefits include reduced security risks, improved compliance, and enhanced operational efficiency.
Addressing user resistance is equally important. Providing clear communication and training on the new system is key. This ensures users understand the reasons for the change and how it impacts their daily workflows. This transparency fosters shared responsibility and promotes user adoption.
Real-World Timelines And Resource Requirements
Successful NAC implementations in the MEA region require realistic timelines and adequate resources. Consulting with experienced security professionals who have deployed NAC in similar environments can offer valuable insights. They can provide realistic estimates of the required time and resources, including personnel, budget, and technical expertise. Understanding your organization’s specific needs based on size and complexity is also critical for effective planning.
The growth of proximity access control is worth noting. Crucial for granting or restricting network access, this market segment is expected to grow from USD 75.26 million in 2025 to nearly USD 99.30 million by 2030 in the MEA region. This highlights the increasing use of proximity-based authentication.
Measuring Implementation Success
Defining clear metrics for success is vital. These should go beyond basic compliance checks. Consider factors like reduced unauthorized access attempts, improved incident response times, and an enhanced overall security posture.
Tracking these metrics allows organizations to demonstrate the tangible benefits of their NAC investment and justify ongoing support. This data is also valuable for refining and optimizing the NAC system over time. For more information, read: How to Reduce Network Downtime.
By following these practical guidelines, organizations in the MEA region can implement network access control effectively. This approach minimizes disruption and maximizes security outcomes, creating a more secure and resilient network environment. This allows businesses to focus on growth and innovation.
Unified Defense: When Physical and Network Access Converge

The line between physical security and network security is blurring. Leading MEA enterprises are adopting unified security approaches, treating physical and network access control as integrated components of a comprehensive security strategy. This creates a significantly stronger security posture, allowing organizations to respond to threats more effectively and efficiently.
The Benefits of Integrated Security
Integrating physical and network access controls offers several key advantages. It helps prevent blended attacks that combine physical intrusion with cyber threats. Unified systems also streamline security operations, simplifying management and reducing complexity. This allows security teams to focus on proactive threat management rather than juggling disparate systems. This integration is vital for organizations looking to bolster security and optimize operational efficiency.
Location Data for Smarter Decisions
Modern security teams are leveraging location data to improve access control decisions. Consider a scenario where access to a secure server room is granted only when an employee’s badge is scanned and their network credentials are authenticated. Using this contextual information strengthens security and enhances operational flow. Organizations can shift from static security measures to a more dynamic and adaptive security model.
In 2024, the access control market in the Middle East and Africa, a crucial element of network access control systems, reached a value of USD 1008.9 million. Hardware, such as biometric and card readers, dominated this market.
Unified Credentials Across Boundaries
Implementing unified credential systems is another critical aspect of converged security. A single credential, like an employee badge, can be used for both physical access (entering the building) and network access (logging onto a computer). This simplifies user experience and tightens security by minimizing potential access points. It also reduces the administrative burden of managing multiple credential systems. This allows for consistent policy enforcement across both physical and digital domains.
Coordinated Security Response
Converged security also enhances incident response. By connecting workflows between traditionally separate physical security and IT teams, organizations can react to security incidents more quickly and efficiently. For instance, during a breach, both physical and network access can be instantly restricted, mitigating potential damage. This represents a substantial improvement over traditional, siloed response models. For further information on preventing network downtime, see: How to Prevent Network Downtime.
Integration Models and Industry Considerations
Various integration models cater to different organizational maturity levels. Organizations can start with basic integrations and gradually progress toward fully unified systems. This phased approach allows for a smooth transition and minimizes disruptions. Specific industries, like finance and healthcare, have heightened security requirements and stricter compliance mandates. These often necessitate advanced features like real-time monitoring and automated response systems.
Next-Generation NAC: Staying Ahead of Evolving Threats
The threat landscape is constantly evolving, requiring organizations to adapt their security strategies. Network Access Control (NAC) is no exception. Forward-thinking organizations, particularly in the Middle East and Africa (MEA) region, are adopting advanced NAC technologies to address these evolving threats. These new capabilities are transforming traditional access control models into proactive and dynamic defense systems.
The Rise of Behavioral Analytics and Machine Learning
Modern NAC solutions are integrating behavioral analytics and machine learning to enhance security. These technologies establish a baseline of normal network activity for users and devices. Any deviation from this baseline, such as a user accessing unusual files or a device connecting from an unexpected location, triggers an alert. This proactive approach allows potential threats to be identified and addressed before they escalate into security incidents.
Contextual Awareness for Smarter Access Decisions
Contextual awareness is another key feature of next-generation NAC. Access decisions are made based on a variety of factors, including user identity, device posture, location, time of day, and the resource being accessed. This allows for more granular control. For instance, a user might have access to certain applications during business hours but be blocked from accessing them after hours or from an unmanaged device. This nuanced approach strengthens security without unduly restricting legitimate access.
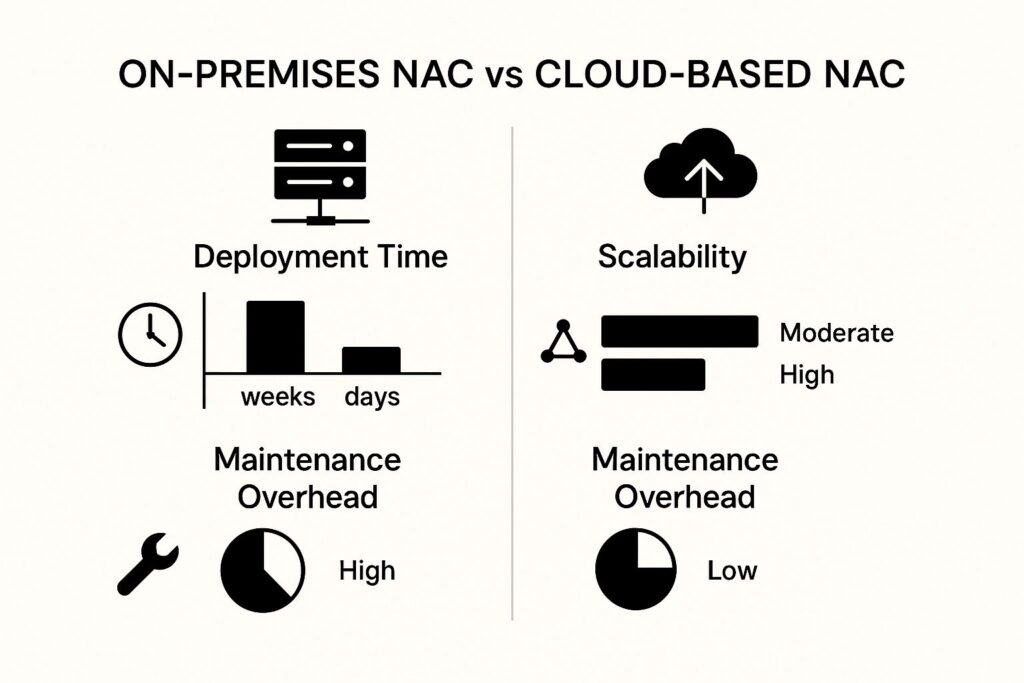
This infographic compares on-premises and cloud-based NAC solutions. It highlights key differences in deployment time, scalability, and maintenance overhead. Cloud-based NAC offers faster deployment, greater scalability, and reduced maintenance compared to on-premises solutions, making it an attractive option for organizations seeking agility and cost-effectiveness. For more information on IT infrastructure management in the MEA region, you can read this article: How to master IT Infrastructure Monitoring in MEA.
Continuous Authentication: Beyond the Initial Login
Unlike traditional NAC systems that focus on initial login verification, next-generation NAC employs continuous authentication. User access is constantly monitored and re-evaluated throughout the session. If suspicious activity is detected, access can be revoked immediately, even after the initial login. This added layer of security prevents unauthorized access from persisting undetected.
Zero Trust and Microsegmentation: Limiting the Blast Radius
Many MEA organizations are combining NAC with zero-trust architectures. Zero trust operates on the principle of “never trust, always verify,” granting access only on a need-to-know basis, even for users and devices already inside the network. Coupled with microsegmentation, which divides the network into smaller, isolated zones, this approach significantly limits the impact of a security breach. If one segment is compromised, the attacker’s ability to move laterally within the network is restricted.
To better understand the various next-generation NAC technologies available, let’s look at the following comparison:
Advanced NAC Technologies Comparison
Evaluation of emerging NAC technologies based on security effectiveness, implementation complexity, and business value
| Technology | Security Enhancement | Implementation Complexity | Business Value | Regional Adoption |
| Behavioral Analytics | Detects anomalies and insider threats | Moderate | Proactive threat detection | Increasing in MEA |
| Machine Learning | Automates threat identification and response | High | Reduced response times | Growing in MEA |
| Contextual Awareness | Granular access control based on context | Moderate | Improved security posture | Emerging in MEA |
| Continuous Authentication | Ongoing access monitoring and validation | Moderate | Prevents persistent threats | Increasing in MEA |
| Microsegmentation | Limits breach impact through network isolation | High | Reduced attack surface | Growing in MEA |
This table summarizes how each technology contributes to improved security, its implementation challenges, and the resulting business benefits. The regional adoption column reflects the current trends observed in the MEA region.
Implementing Next-Generation NAC: Practical Strategies
Adopting these advanced NAC technologies doesn’t necessitate a complete overhaul. Organizations can integrate these features incrementally into their existing security frameworks. Starting with behavioral analytics for critical systems, for example, can provide immediate security benefits. Organizations can then expand to continuous authentication and microsegmentation. This phased approach ensures a smoother transition and minimizes disruptions.
Case Studies: Real-World Impact
Practical implementations of next-generation NAC are delivering impressive results across various sectors, including financial services, healthcare, and critical infrastructure. Organizations are reporting significant reductions in security incidents, faster threat detection, and improved compliance. These successes highlight the value of investing in a robust and forward-looking network access control strategy.
Navigating MEA Compliance with Strategic NAC Solutions
Regulatory compliance is essential for businesses operating in the Middle East and Africa (MEA). Rather than a burden, compliance should be seen as a strategic opportunity, strengthened through robust Network Access Control (NAC). This guide outlines how to meet diverse MEA regulatory requirements while enhancing your security posture.
Translating Regulatory Frameworks Into Actionable NAC Policies
Many MEA regulatory frameworks, especially those covering data protection and critical infrastructure, have specific requirements for access control. A strategic NAC solution translates these complex requirements into practical, actionable policies. For example, regulations requiring multi-factor authentication are easily implemented and enforced through NAC. This allows organizations to meet compliance mandates and simultaneously boost their overall security.
Streamlining Documentation For Auditors
Audits are a regular part of compliance. A well-implemented NAC system significantly simplifies this process. NAC solutions with thorough logging and reporting features easily generate the necessary documentation for auditors. This reduces administrative overhead and ensures your organization is always audit-ready, saving time and resources while demonstrating your commitment to compliance.
Addressing Multiple Compliance Requirements With A Single Solution
MEA countries often have overlapping, yet distinct, regulations. A key NAC advantage is its ability to address multiple compliance requirements with one solution. By centralizing access control policies and enforcement, NAC simplifies compliance management across different jurisdictions. This eliminates the need for separate solutions for each set of requirements, increasing efficiency and reducing complexity.
NAC Features and Regional Regulations
Specific NAC features directly support regional regulations. Device profiling and posture assessment help organizations meet endpoint security requirements. Features like user access review and privileged access management are crucial for adhering to data governance regulations. Choosing a NAC solution with these key features proactively addresses various compliance obligations.
Managing Cross-Border Data Flow Restrictions
Data sovereignty and cross-border data flow are increasingly important in the MEA region. NAC solutions help manage these complex restrictions by controlling access to sensitive data based on user roles and location. Organizations can configure policies that restrict access to certain datasets from specific countries, or permit only authorized personnel to access data from other jurisdictions. This granular control ensures compliance with data flow regulations while facilitating business operations.
Future-Proofing Your Compliance Strategy
The regulatory environment is constantly changing. A flexible and scalable NAC solution is essential for future-proofing your compliance strategy. Select a NAC solution adaptable to new regulations and integrable with other security tools. This ensures your organization adapts to future regulatory changes and maintains compliance without major system overhauls, allowing your organization to stay ahead of the curve.
Sector-Specific Guidance for MEA Organizations
Different sectors face unique regulatory challenges. Financial institutions in the MEA region, for instance, face stringent data security and customer privacy regulations. Healthcare organizations must comply with strict patient data protection requirements. A well-designed NAC solution assists these sectors in meeting their specific compliance obligations, protecting sensitive information, and adhering to industry best practices. This tailored approach aligns security measures with each sector’s specific risks and regulatory requirements.
The Future of Network Access Control in MEA
The Middle East and Africa region is undergoing significant digital transformation, presenting both exciting opportunities and complex security challenges. This necessitates a proactive and future-focused approach to network access control (NAC). Let’s explore the emerging trends and technologies reshaping how organizations in the MEA region are safeguarding their networks.
AI-Powered Security: The Next Frontier
Artificial intelligence (AI) is playing an increasingly vital role in network security. AI-powered NAC solutions can analyze large volumes of data to detect anomalies and potential threats in real time. This proactive approach empowers security teams to respond to incidents swiftly and effectively, minimizing potential harm. This represents a considerable advancement over traditional, reactive security methods.
Passwordless Authentication: Moving Beyond Passwords
Passwordless authentication is gaining momentum in the MEA region as organizations strive to enhance security and user experience. Biometrics, hardware tokens, and magic links are replacing traditional passwords, mitigating the risk of phishing attacks and password breaches. This shift also simplifies the login process, making access more convenient without compromising security.
Decentralized Identity: Empowering Users
Decentralized identity models are emerging as a valuable tool for managing digital identities. This approach provides users with greater control over their personal data and streamlines authentication across various platforms and services. By reducing reliance on centralized identity providers, decentralized identity strengthens both privacy and security. This is particularly important in our increasingly data-driven world.
Cloud-Native NAC: Adapting to Modern Infrastructures
Cloud adoption is rapidly increasing in the MEA region, and NAC solutions are adapting to accommodate this change. Cloud-native NAC provides scalability, flexibility, and cost-efficiency, making it well-suited for managing access within dynamic cloud environments. This adaptability is essential as organizations increasingly depend on cloud services and distributed workforces.
Investing in the Future of Security
Selecting the right security investments is critical for the long-term success of organizations in the MEA region. Prioritizing solutions that integrate AI, passwordless authentication, decentralized identity, and cloud-native architectures will enable your organization to address the complexities of the evolving digital environment. These technologies empower proactive security measures and enhance organizational agility, allowing businesses to thrive amidst growing cyber threats.
Ready to strengthen your network security? Discover how FSI Technology can assist your organization in developing a robust and future-proof network access control strategy. Visit us today to explore our comprehensive suite of Cisco solutions and expert services.
